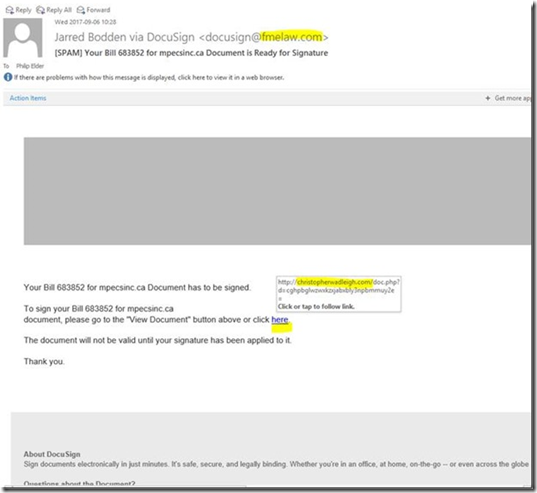
The first place in any “security strategy” should be to train the human. Most malware infections today are caused by a user clicking through when they should not have. The posters below give a very clear set of workflows for an infection. Excellent posters via MALWARE-TRAFFIC-ANALYSIS.NET Note the STEP IN […]
Malware
2 posts
With the abundance of malware and ransomware it’s absolutely necessary that we take the time to examine our virtualization host and backup structures. Volume Shadow Copies Obviously not a “backup” Most ransomware kills all shadow copies available on a system Backup to Disk/NAS/SAN Disk Rotated NAS/SAN needs to be streamed […]