We completed a custom server build yesterday. Intel R2208WFTZSR 2U dual Intel Xeon Processor Server System Dual Intel Xeon Processor 6240Y 192GB ECC RAM (12x 16GB) Intel RAID Controller and Intel RAID Maintenance Free Backup Unit (2) 240GB Intel SSD M.2 RAID 1 (2) 3.8TB Intel SSD D3-S4510 SATA RAID […]
How-To
Reading this article on Serve The Home this morning: Kingston DC450R SSD Released SATA and 3.84TB Maximum. The Kingston DC450R SSD is being released with “Data Center Series” on the sticker. But, it does not have power loss protection (PLP) so how could this be? The suspicion here is that […]
The HILTI Adaptive torque module has a software component that needs to be downloaded for programing, management, and reporting. HILTI Adaptive Torque Module SI-AT-A22 The instruction booklet mentions the need to obtain the AT Documentation Software but it was not readily apparent where we were to get the software. The […]
We started getting alerts from JetPack that our WordPress site, https://blog.mpecsinc.com, was offline. Sure enough, browsing to the site lead to a “This site is experiencing technical difficulties.” white page. Since our WordPress site is hosted in Azure, we logged on to the portal and clicked into the AppService blade […]
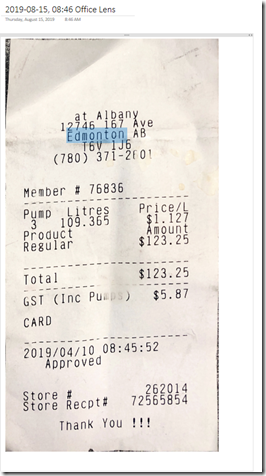
Throughout the day we can process quite a few credit card and debit transactions. Getting those receipts into our bookkeeping system can be a challenge. Enter Microsoft’s Office Lens app. Office Lens on iPhone – Co-op Albany Fuel Receipt Start the app and point it at the receipt in question. […]
We’re in the process of custom building an Intel Xeon Processor E-2278G series workstation. The graphics card that’s being installed is the AMD RADEON PRO WX 3100. The system will be driving three monitors with two across the bottom and one above middle to them. When getting ready to install […]
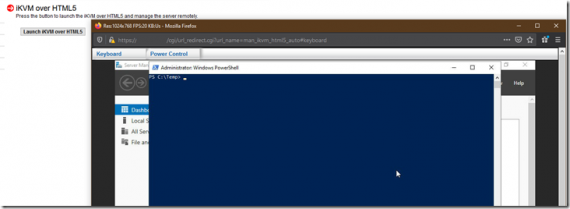
One of our standalone Hyper-V hosts was experiencing performance issues with the Remote Desktop Session Host that provides the company’s primary user environment. The main application running on the session host can be a bit finicky so we ran the gamut troubleshooting within the guest OS. The performance drags were […]
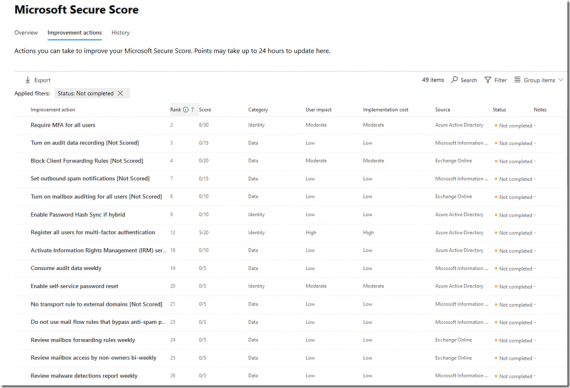
We’re in the process of digging in to the methodology for securing our Office 365 (O365) and Azure resources. One of the things we are doing is building an on-boarding checklist for setting up O365 and Azure tenants as we sign them up. The first place to start is the […]
The first place in any “security strategy” should be to train the human. Most malware infections today are caused by a user clicking through when they should not have. The posters below give a very clear set of workflows for an infection. Excellent posters via MALWARE-TRAFFIC-ANALYSIS.NET Note the STEP IN […]
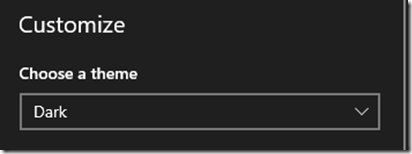
This was something learned this morning: Dark Mode for virtually all apps that can do it! If there’s one thing we’ve discovered, LCD/LED monitors are intense on the eyes. At times, it can be like not wearing sunglasses on a sunny day outside with snow on the ground: Snow Blind. […]