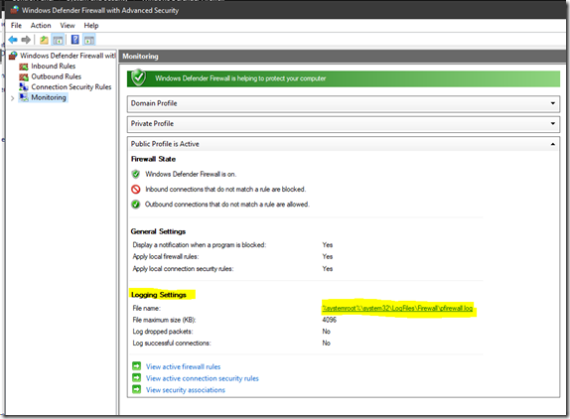
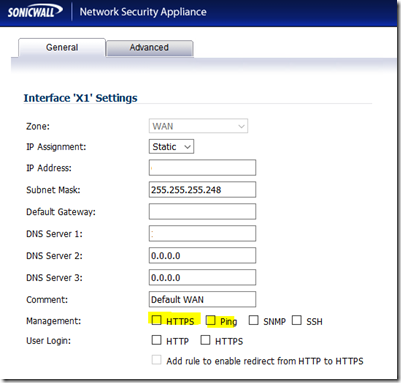
When we set up a greenfield Active Directory Forest and Domain we do the following in Group Policy: New Group Policy Object (GPO) Linked & Enforced at the domain Level: Default Domain Security Policy Enable Remote Desktop Inbound: Allow users to connect remotely by using Remote Desktop Enable the Windows […]
Security
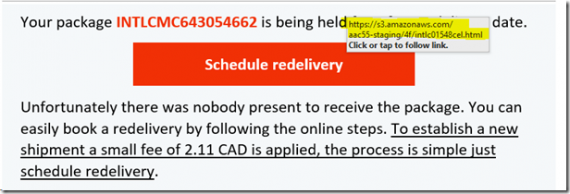
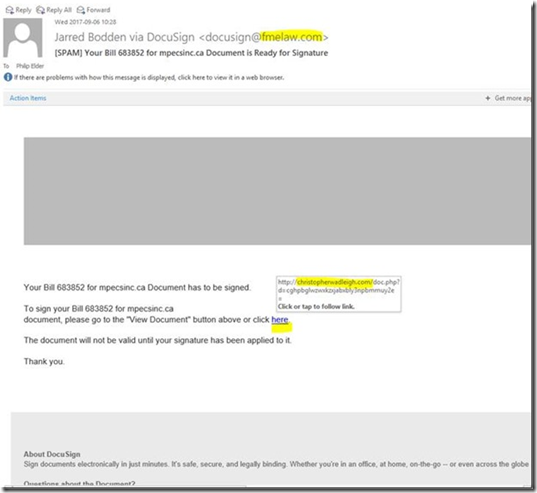
It’s pretty obvious that we’re in the height of the Christmas purchasing season. So, when something like this shows up in the Inbox if one isn’t thinking, one clicks and pays. Right? Well, in this case the Scrooge McDuck won out over paying the “fee” so a search of Intelcom’s […]
We’ve taken to deploying a Cloud Witness for almost all of our Windows Server based clusters whether Hyper-V, Storage Spaces Direct (S2D), or Scale-Out File Server. When logging on to the Azure Portal this morning we were prompted to check out a number of different areas by the Azure Advisor. […]
As the subject says, there is basically an open door in the way RD Gateway handles incoming packets. Whether it is being exploited in the wild as of this writing is questionable. That being said, this is a bad one folks. Get those RD Gateway servers patched up. Oh, and […]
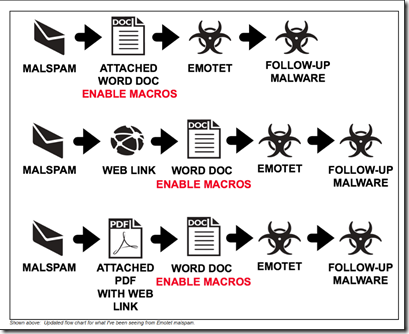
The following is a list of things we can do to help protect our client’s networks from a Ransomware Attack or recover from one if someone does end up doing something they should not have. Train users to not click ENABLE MACROs. Image Credit: https://www.malware-traffic-analysis.net Remember, those little EXTERNAL flags […]
This news is more than disappointing: Personal and Social information of 1.2 billion people Discovered in Massive Data Leak The old cliché: Ignorance is Bliss Anyone else out there not know what “Data Enrichment” is and that there are companies out there that do this and then sell that information? […]
There have been a number of vulnerabilities published for the Remote Desktop Services protocol stack over the last little while. The catch with all of them is to have a RDP listener open to the Internet on any port with Network Level Authentication disabled or not available as it was […]
We don’t receive a lot of these kinds of messages from SonicWALL so when it came in it was treated with much suspicion. The message can be found here: SonicWALL Security Advisory Announcement Below is a quote with all of the tracking stuff removed from the URLs. July 19, 2019A […]
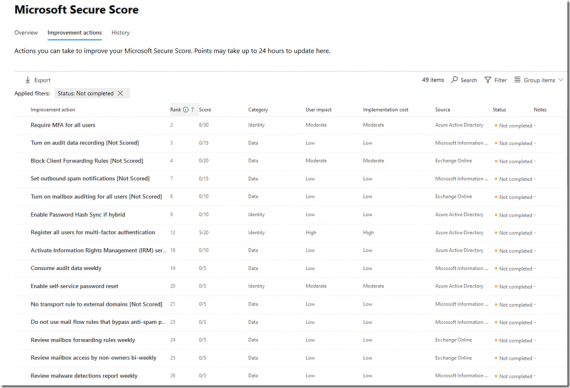
We’re in the process of digging in to the methodology for securing our Office 365 (O365) and Azure resources. One of the things we are doing is building an on-boarding checklist for setting up O365 and Azure tenants as we sign them up. The first place to start is the […]
The first place in any “security strategy” should be to train the human. Most malware infections today are caused by a user clicking through when they should not have. The posters below give a very clear set of workflows for an infection. Excellent posters via MALWARE-TRAFFIC-ANALYSIS.NET Note the STEP IN […]