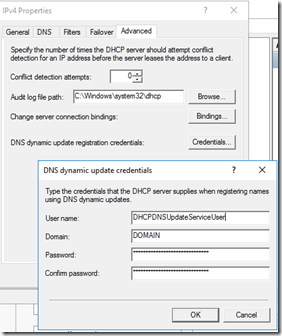
The following is a list of things we can do to help protect our client’s networks from a Ransomware Attack or recover from one if someone does end up doing something they should not have.
- Train users to not click ENABLE MACROs.
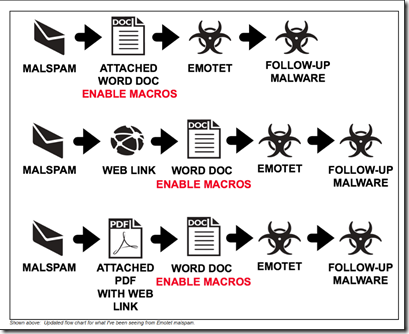
- Image Credit: https://www.malware-traffic-analysis.net
- Remember, those little EXTERNAL flags in e-mails become background noise to the human eye/brain!
- Remove, and I mean REMOVE, SMBv1 (Remove-WindowsFeature FS-SMB1 -Restart) everywhere.
- If needed for crappy old copiers and scan to folder then workgroup VM with user READ access account and copier account MOD on the shared folder.
- Emotet is using a now two year old revealed vulnerability in SMBv1. There is absolutely NO reason for it to move laterally today!
- We know of IT that have given up “it’s doing no harm” instead of updating their images to remove/disable SMBv1!
- Never join Hyper-V hosts to guest’s domain
- Cluster: Set up a RAID 1 array of 250GB or more on cluster nodes and configure a DC on 2 for separate cluster ADDS
- BACKUP
- Off-Site backup with air-gap
- GFS (Grandfather, Father, and Son)
- 3-2-1 Rules Apply (Three Mediums for those Backups)
- Back up Cloud Services (Veeam for O365 for example)
- All y’all are aware that the onus is on the end user/company to back up cloud data?
- Remote Desktop Services published properly behind RD Gateway/Broker/Web
- Two Factor via DUO or Microsoft MFA for extra security
- Isolate Windows 7 and Server 2008 blocking all Internet access
- Use Group Policy with Windows Firewall to tailor inbound/outbound packet flow to needed services only.
- VLAN/Segment
- Use a Jump Server for management
- Privileged Access Workstation
- Honey Pot files and folders (FSRM)
- Edge with decent security suite helps but not a lot
- A router like a SonicWALL or other business class setup
- Edge BLOCK/DENY by default and allow:
- 80/443 outbound for all _client_ endpoints (RDS exception – NO servers)
- 53 TCP/UDP DNS from DCs ONLY
- SMTP inbound from sanitation provider ONLY (prevents SMTP AUTH attacks against on-premises Exchange)
- SMTP outbound from on-premises Exchange and MFPs ONLY – Use sanitation/continuity as SmartHost
- And yes, virtually all of our clients are on-premises Exchange 2013, 2016, and 2019!
- 3389 TCP or alternative ports published inbound for RDP NO. NO. NO. NO. NOOOOO!!!!!
- ** Use RD Gateway and DUO/Microsoft MFA if needed.
- SSL VPN for access to network if required
- Restrict Usernames and Passwords or manage closely if high user churn
- Custom ports are sometimes required. We find out pretty quickly just what is trying to sneak out of our networks!
- Audit the following (PowerShell is great for this)
- Domain User Accounts
- Last Logon Date for User and Computer Objects
- Windows OS version levels
- Files and Folders ownership, access dates, and more (FSRM)
- Make sure all MSP Tools and Utilities are UP TO DATE!!!
- Pay attention to vulnerability and security reports from vendors
- Lots of examples of flaws exploited in third party software to gain access to MSP’s client networks
The above represents an off-the-top of what we can do to protect our client’s network infrastructure.
The following post goes into a lot more detail: Protecting a Hyper-V Host and Backup Repository from Malware and Ransomware
There’s also links in that post to more reading and detail.
Happy New Year everyone! 🙂
Philip Elder
Microsoft High Availability MVP
MPECS Inc.
www.s2d.rocks !
Our Web Site
PowerShell and CMD Guides